
CF-Cannon V2 is a tool written in python to perform layer 7 stress tests on your own server.
V2 version enables distributed attack on each node with penetration of the UAM page and can be (theoretically) deployed on infinite machines.
Disclaimer: Please make sure all your tests are legal and with the consent of relevant parties as I won’t be responsible for any consequence caused by this script.
Install:
apt-get update apt-get -y upgrade apt-get install build-essential nodejs python-setuptools apt-get install -y python-pip pip install demjson Flask pycurl
Run: (On each node)
python attack.py
Then use any third party API Tester: (i.e https://apitester.com/)
POST a JSON request to path written in attack.py (Default: /attack)
attackinfo={
"T": 8,
"charset": "utf-8",
"is_protected_by_cf": false,
"keywords": "welcome",
"path": "/index.php",
"peerCount": 300,
"threadCount": 10000000,
"url": "http://www.sample.com"
}
After sending a POST request, you’re supposed to see this:
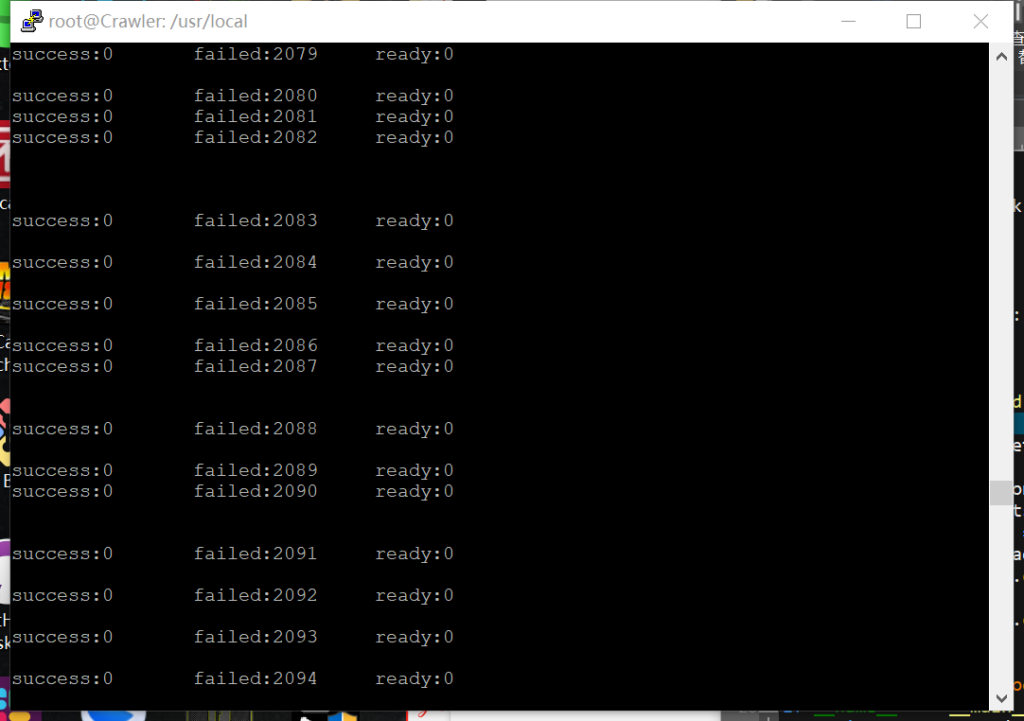
Failed means your node has no access to the target (keyword not found). It can be caused by:
- You have already taken it down (Success)
- Wrong keyword on page or path can’t be found
- Your IP/Machine is on the blacklist
- Any other reason that may cause you to have no access to a certain page
Success simply suggest target web page still functions normally
[wpedon id=”461″ align=”center”]
Check github I’m pretty sure you’ll get plenty of them
Start a new issue on Github and attach all your output
Hello,
I was asking me how to add multible nodes?
Like:
app.run(host=’0.0.0.0′,port=80)
app.run(host=’0.0.0.0′,port=80)
app.run(host=’0.0.0.0′,port=80)
?
And can host be a Domain?
don’t work for me ( import pycurl )
python27 no support pycurl ( i can’t install pycurl witch python27 )